Passkeys
As Web3 reshapes the digital landscape, introducing decentralized and trustless operations, there’s an emerging need for heightened security measures. Enter the concept of Hardware Sign, an innovative approach that promises to take digital identity verification to new heights. So, what exactly is Hardware Sign? At its core, Hardware Sign is the principle of using a device’s dedicated microchips, like Secure Enclaves, to prove a user’s identity. Rather than relying on external servers or online platforms, the authentication process occurs right within your device. Hardware Sign’s significance stems from its localized approach to identity verification. By keeping the authentication process confined within the device, it drastically reduces the risk of online breaches or middlemen interference. Furthermore, it leverages the intrinsic security features of modern devices, ensuring that even if a device is lost or stolen, the data within the Secure Enclave remains protected. In the continuously evolving world of digital security, the introduction of the Secure Enclave marks a significant step forward. But what is it, and how does it change the game, especially in the context of Web3?Understanding the Secure Enclave
The Secure Enclave is an advanced hardware feature, specifically designed to act as a protective shield around users’ most sensitive data. Unlike other parts of a device, which might handle everything from app processes to notifications, the Secure Enclave is a distinct microchip, isolated from all other components of the device. This separation ensures that sensitive data, such as biometric information and cryptographic keys, are isolated from potential threats that might compromise other parts of a device. Learn more hereAccessing the Secure Enclave
Another key aspect of the Secure Enclave is its fortified access mechanisms. Data stored within it can only be accessed through either a passcode or biometric authentication methods like Face ID or Touch ID. This adds an extra layer of security, making sure that even if a device falls into the wrong hands, the data within the Secure Enclave remains secure.Integrating Secure Enclave into Web3
Perhaps the most groundbreaking feature of the Secure Enclave, especially in the realm of Web3, is its support for Elliptic Curve Cryptography (ECC). This means that the Secure Enclave can generate and manage cryptographic key pairs, crucial for digital transactions and identity verification in the Web3 ecosystem. Even more impressive is the capability of the Secure Enclave to sign messages using the internally generated key, without ever allowing the extraction of the key from its confines. In practical terms, this ensures the highest level of data security, as the key never leaves the safety of the Secure Enclave, eliminating potential points of vulnerability. For Web3 users, this has profound implications. Instead of remembering a 12-word mnemonic phrase to access their accounts — a cumbersome process for many — users can simply use their biometric data. When a user employs, say, their fingerprint via Touch ID, the Secure Enclave verifies the biometric data, signs the necessary cryptographic messages internally, and grants access. This seamless process not only enhances security but also provides an intuitive and user-friendly experience.Our Key Management Approach
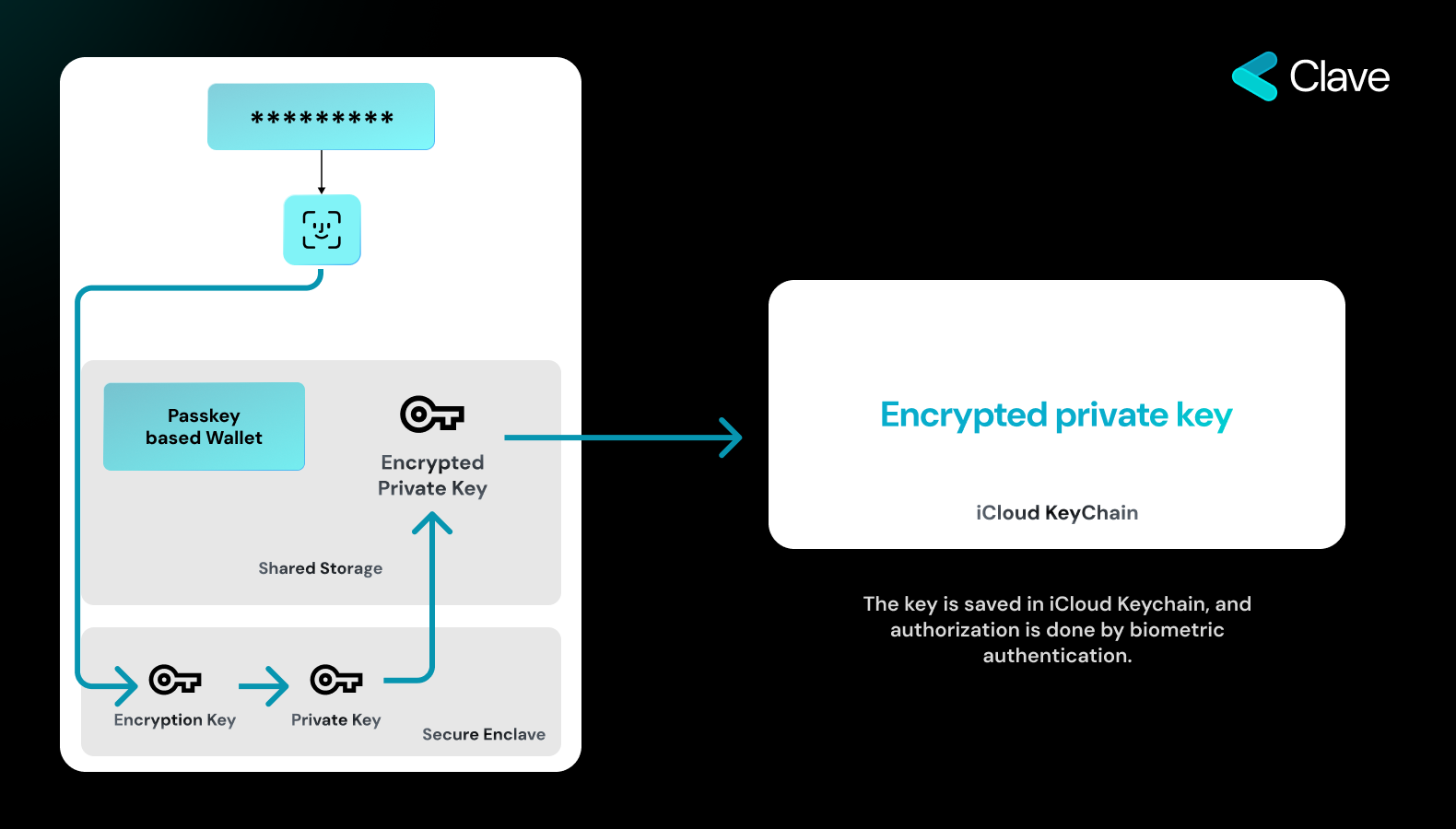
At the core of our approach is the utilization of Secure Enclaves. The cryptographic key, essential for your transactions, is generated within this enclave and importantly, it never leaves its confines. This encapsulation ensures the key’s security even during transaction processes.The Key Creation Process
The journey starts when a user decides to generate a cryptographic key pair. Here’s how it unfolds:- Biometric Authentication: The user initiates the key generation process by providing biometric authentication, such as a fingerprint or facial recognition. This step ensures that only the genuine user can authorize the creation of a key pair within the Secure Enclave.
- Internal Key Generation: Post authentication, the Secure Enclave creates the cryptographic key pair. The essential factor to note here is that the generated key remains within the Secure Enclave, never venturing outside, ensuring its absolute security.
The Transaction Process
Once the key is securely generated, it can be used to sign messages, a fundamental step for initiating transactions in the Web3 world. The process is straightforward yet robust:- Initiating the Signing Process: When a user wishes to make a transaction, the app takes the required message and forwards a signing request to the Secure Enclave.
- Biometric Authentication for Signing: To confirm the signing request, the user provides biometric authentication once again. This step ensures that only the authorized user can approve the signing of a message using the stored key.
- Internal Message Signing: The Secure Enclave, upon receiving user authorization, signs the message with the key created inside the Secure Enclave.
- Ready for the Blockchain: The signed message is now in a transaction format, primed and ready to be recorded on the blockchain.

What If The User Loses The Device?
What If The User Loses The Device?
A genuine concern, but there’s a silver lining. With Secure Enclave, even if your device falls into the wrong hands, accessing sensitive information is next to impossible. But how do you recover your account? Read more about recovery here.

